News
Feds: Google AI Trade Secrets Stolen by Own Engineer
A former Google software engineer has been arrested on four counts of theft of confidential information related to Google's generative AI technologies.
The U.S. Department of Justice this week announced the arrest of Linwei Ding, a Chinese national living in Newark, Calif., for pilfering AI-related trade secrets from Google between 2022 and 2023 while he was employed at the company. He is also accused of being involved in dealings with China-based AI startups, presumably using the information he stole from Google as lure for investors.
According to the indictment filed Tuesday with the U.S. District Court for the Northern District of California, Ding is accused of stealing proprietary Google information related to "the hardware infrastructure and software platform that allow Google's supercomputing data centers to train large AI models through machine learning."
Google uses custom third-party GPUs and its own Tensor chips to power machine learning and AI workloads in its datacenters (the "hardware infrastructure" referenced in the indictment), and a cluster management system to automate model training tasks (the "software platform").
Ding, whom Google hired in early 2019, was primarily involved with the software side of Google's supercomputing project, though he also had authorized access to information about the hardware. He is alleged to have stolen over 500 files worth of data related to these technologies, periodically siphoning them from Google's network into his personal Google account starting in May 2022 until May 2023.
Also during that same time, unbeknownst to Google, Ding apparently became the CTO of one Chinese AI startup and the founder and CEO of another, occasionally traveling to China to find local investors. The company that he founded, according to the indictment, described itself this way: "[W]e have experience with Google's ten-thousand-card computational power platform; we just need to replicate and upgrade it and then further develop a computational power platform suited to China's national conditions."
Ding was able to bypass multiple layers of Google's security. According to the indictment, Google constantly monitored employee activity on its network, logging data transfers and IP addresses, requiring devices to be authenticated before accessing its network, and implementing two-factor authentication when employees sign on to their work accounts. Employees are also required to wear badges to enter Google facilities and tell their managers whenever they're working remotely from abroad. Employees working from China, North Korea and Iran automatically had their network access limited.
Ding found several chinks in Google's armor, however. To make it appear like he was working from Google's offices while he was in China, he gave his badge to a Google coworker so they could scan it at the building for him. And to swipe files from Google's network, he "[copied] data from the Google source files into the Apple Notes application on his Google-issued MacBook laptop [...] then converted the Apple Notes into PDF files and uploaded them from the Google network into" his personal account.
Google did not begin investigating Ding in earnest until the end of 2023. By then, Ding had already purchased a one-way ticket from San Francsico to China and given Google his notice of resignation. After learning that Ding had appeared at a conference in Beijing representing the company that he founded there, Google locked his laptop, searched through his activity logs and discovered the transfers of stolen data. The Federal Bureau of Investigation became involved shortly after.
The summary of the charges against Ding are below:
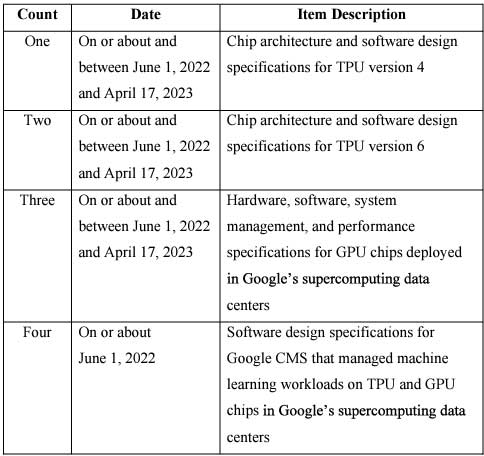
"If convicted," according to the DoJ announcement, "Ding faces a maximum penalty of 10 years in prison and up to a $250,000 fine for each count."
The DoJ characterized Ding's actions as a threat to U.S. national security. "In this case, we allege the defendant stole artificial intelligence-related trade secrets from Google while secretly working for two companies based in China," said Attorney General Merrick Garland in a prepared statement. "We will fiercely protect sensitive technologies developed in America from falling into the hands of those who should not have them."
Deputy Attorney General Lisa Monaco indicated that the DoJ is "on high alert to" AI's risks and that it "will relentlessly pursue and hold accountable those who would siphon disruptive technologies -- especially AI -- for unlawful export."